



Unveiling the Power of
AI-Driven Code Analysis
At Privya, we've pioneered a groundbreaking approach for data flow mapping that leverages advanced AI and machine learning techniques to analyze code. This innovative method allows us to map data flows across entire software ecosystems without the need for runtime analysis or manual documentation.
Trusted by Industry Leaders

Static Code Analysis
We parse and analyze your entire codebase, transforming it into a comprehensive abstract syntax tree.

Contextual Understanding
We extract crucial metadata from comments, variable names, and code structure to provide rich context about data types and purposes.

Dynamic Graph Modeling Construction
We create a graph representation of the code to provide the model with a useful vantage point into the data's key qualities.

AI-Powered Data Flow Tracing
Our proprietary algorithms identify and track data movement from source to sink, through variable assignments, function calls, and API interactions.

Comprehensive Framework Recognition
Our extensive knowledge base allows us to understand data interactions beyond explicit code, covering thousands of common libraries and frameworks.
The Visionary Behind the Innovation: Dr. Uzy Hadad
Dr. Uzy Hadad is the co-founder and CTO of Privya. Inspired by the recent improvement in large language models (LLMs) and the ability to consider code as a natural language (like in AI code generators such as Co-Pilot), Dr. Uzy has devoted his research to the study of graph theory and its practical applications in computer science. With over a decade of experience in data engineering, data science, and global technology transformation, Dr. Uzy's work has revolutionized how we understand and visualize complex data relationships.
His academic background includes a PhD in Mathematics and Computer Science from The Hebrew University of Jerusalem and post-doctoral studies in Mathematics and Computer Science at the Weizmann Institute of Science, one of the highest-ranked institutions globally. Dr. Uzy's pioneering work in applying graph theory and machine learning to static code analysis has laid the foundation for Privya's unique approach to data lineage. His algorithms have redefined what's possible in terms of understanding data flows without runtime execution, bridging the gap between engineering, privacy, compliance, and data protection teams.



In today’s intricate digital ecosystems, data runs through applications like lifeblood. At Privya, we illuminate these hidden streams, mapping the subtle interconnections that define our technological landscape. Our mission: to map these data flows with precision, safeguarding privacy and ensuring compliance at every juncture.
– Dr. Uzy Hadad
In-Depth Technology Breakdown
AI-Driven Code Scanning
Privya's AI-driven code-scanning technology forms the foundation of our solution.
Key Features:
- Map, discover and visualize data flows across your software ecosystem.
- Automatic identification and categorization of PI, SPI, and critical data
- Comprehensive scanning across the entire software development lifecycle
- Near real-time visibility into potential privacy risks
- Customizable scanning parameters for any regulation or corporate policy
Technical Deep Dive:
Our AI utilizes advanced natural language processing (NLP), information retrieval concepts, and machine learning models trained on millions of code samples. The system employs a multi-stage analysis pipeline:
- Lexical Analysis: Tokenizes code into meaningful elements and embed it in a large language model
- Syntactic Analysis: Constructs an abstract syntax tree (AST)
- Graph representation of the code
- Semantic Analysis: Interprets code meaning and data flow
- Pattern Matching: Identifies known data patterns and structures
- Contextual Analysis: Considers surrounding code and comments for improved accuracy


Data Lineage Mapping
Our comprehensive data lineage and flow mapping provide unparalleled visibility into data
movement across your entire software ecosystem.
Key Features:
- Automated, real-time data flow mapping across all systems, AI, and third parties
- End-to-end data tracking from origin to destination
- Identification of complex relationships, including indirect data flows and inheritance
- Powerful impact analysis capabilities
Technical Deep Dive:
Privya's data lineage mapping employs a distributed graph database to model data relationships. Our proprietary algorithms include:
- Incremental Graph Updates: Efficiently process code changes in real-time
- Path Optimization: Quickly trace data flows in complex systems
- Relationship Inference: Deduce implicit data connections
- Confidence estimation
- Classification of purpose and entities


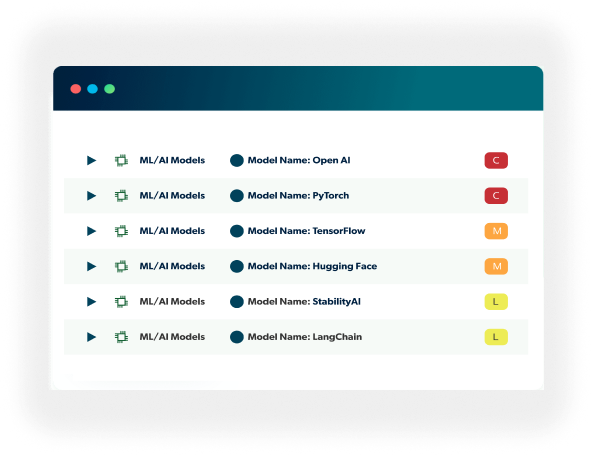
AI/ML Model Detection and Governance
Privya automatically detects and governs AI/ML models within your codebase, ensuring
compliance with emerging regulations.
Key Features:
- Automatic detection and inventory of AI/ML models
- Mapping of thousands of AI/ML frameworks and libraries
- Facilitation of end-to-end AI governance
- Compliance support for EU AI Act and NIST AI RMF
Technical Deep Dive:
Our AI/ML detection system uses a combination of static code analysis and dynamic tracing:
- Framework Detection: Identifies known AI/ML libraries and frameworks
- Data Flow Tracing: Tracks data inputs and outputs to models
- Risk Assessment: Evaluates models for potential privacy issues

Automated Compliance Reporting
Privya generates comprehensive, audit-ready reports tailored to specific compliance needs.
Key Features:
- Automated generation of risk assessments, DPIAs, and ROPAs
- Fully automated data collection and reporting processes
- Rich analytics for risk prioritization
- Customizable reporting templates and workflows
Technical Deep Dive:
Our compliance reporting engine leverages:
- Natural Language Generation (NLG): Creates human-readable report narratives (based on the common templates)
- Risk Scoring Algorithms: Assess and prioritize risks based on multiple factors
- Temporal Analysis: Tracks changes in compliance posture over time
- Regulatory Mapping: Aligns findings with specific regulatory requirements


Audit Capabilities
Privya offers comprehensive audit features to ensure accountability and transparency:
Tamper-Proof Audit Trail:
- An immutable record of all user actions on the Privya platform
- Captures every interaction, modification, and access attempt
- Ensures complete visibility for compliance and security purposes
Granular Access Controls:
- Enforces least privilege principle
- Supports separation of duties
- Customizable user roles and permissions
Historical Audit Retention:
- Maintains comprehensive historical metadata for audit purposes
- Enables trend analysis and long-term compliance tracking
Regulations Supported
Privya offers robust support for a wide range of global privacy compliance standards, including:

GDPR
General Data Protection Regulation

CPRA/CCPA
California Privacy Rights Act/California Consumer Privacy Act

HIPAA
Health Insurance Portability and Accountability Act

GLBA
Gramm-Leach-Bliley Act

PCI DSS
Payment Card Industry Data Security Standard

OCPA
Ohio Consumer Privacy Act

ICDPA
Indiana Consumer Data Protection Act

VCDPA
Virginia Consumer Data Protection Act

MHMDA
Mental Health Modernization and Data Accountability Act

DTDPA
District of Columbia Personal Data Protection Act

CPA
Colorado Privacy Act

EU AI Act
EU Artificial Intelligence Act

NIST RMF
National Institute of Standards and Technology Risk Management Framework
Advanced Algorithms and Methodologies
Privya's cutting-edge technology relies on a suite of advanced algorithms and methodologies to provide unparalleled capabilities. Here's an in-depth look at our algorithmic components:

Abstract Syntax Tree (AST) Generation
- Custom-built parsers for 15+ programming languages, including Java, Python, C++, C, C#, JavaScript, TypeScript, Ruby, and Kotlin
- Incremental parsing for real-time code updates

Data Flow Analysis
Technical Specifications:
- Inter-procedural, context-sensitive analysis
- Support for both forward and backward data flow
- Handling of complex language features (e.g., annotations, inline function)
- Comprehensive coverage across the entire software development lifecycle
- Real-time analysis capabilities for near-instantaneous risk detection
Key Algorithms:
- Taint Analysis: Tracks the flow of sensitive data through the program
- Alias Analysis: Resolves pointer relationships and reference variables
- Constant Propagation: Determines constant values at each program point
- Impact Analysis: Assesses downstream effects of code changes
- Inheritance Tracking: Identifies complex relationships and data flows through class hierarchies

Machine Learning-Based Pattern Recognition
Technical Specifications:
- Ensemble of machine learning models (information retrieval, LLM, statistical models, Transformers)
- Continuous learning from new code patterns and user feedback
- Continuous learning from new code patterns and user feedback
Key Algorithms:
- Transformer-based Code Representation: Captures long-range dependencies in code
- Anomaly Detection: Identifies unusual data handling patterns
- Transfer Learning: Applies knowledge from one language or domain to another

Graph Construction and Optimization
Technical Specifications:
- Distributed graph database for storing code and data relationships
- Support for both directed and undirected edges with multiple attributes
- Real-time graph updates and query capabilities
Key Algorithms:
- Incremental Graph Construction: Efficiently updates the graph as code changes
- Path Compression: Optimizes graph structure for faster querying
- Community Detection: Identifies closely related code and data components
Compliance and Security Features

SOC 2 Type II Attestation
- Demonstrates adherence to strict information security policies and procedures
- Ensures the highest levels of security, confidentiality, and integrity

Advanced Authentication
- Single Sign-On (SSO) support
- Identity federation capabilities
- Multi-factor authentication options

Data Protection
- Advanced encryption for data at rest and in transit
- Secure, geographically distributed data centers for SaaS offering

Network Security
- Sophisticated network segmentation
- Intrusion detection and prevention systems
- Regular security audits and penetration testing

Secure Development Practices
- Follows secure software development lifecycle (SDLC) principles
- Regular code reviews and security testing
Conclusion
Privya's cutting-edge technology offers a comprehensive solution for data privacy, compliance, and governance. By leveraging advanced AI and machine learning, we provide unparalleled insights into your data ecosystem, ensuring compliance, reducing risk, and enabling confident innovation in today's complex data landscape.

